VAPT Services
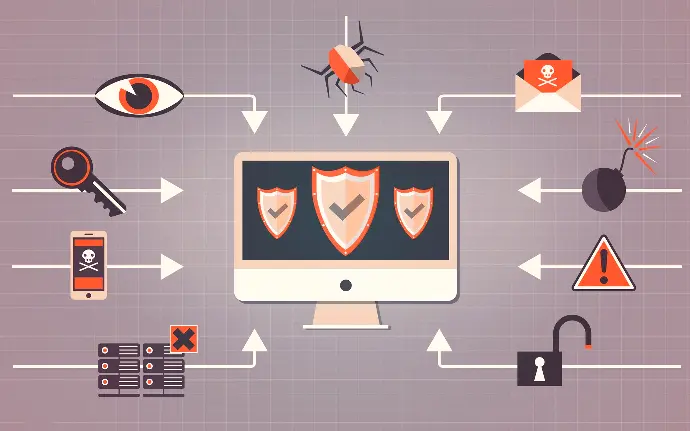
VAPT, at its core, is the process of systematically examining an organization's information systems, networks, and applications to uncover weaknesses that could be exploited by potential attackers. By employing a range of sophisticated scanning and testing techniques, VAPT experts can pinpoint vulnerabilities, assess the associated risks, and provide actionable recommendations for remediation.
The VAPT process typically involves two key stages:
- Vulnerability Assessment: This phase focuses on identifying and cataloging the various security vulnerabilities present within an organization's IT infrastructure. VAPT professionals utilize specialized tools and techniques to scan systems, networks, and applications, uncovering potential entry points and weaknesses
In the face of ever-evolving cyber threats, Vulnerability Assessment and Penetration Testing (VAPT) have emerged as critical components of a robust cybersecurity strategy. These complementary disciplines empower organizations to proactively identify and mitigate security vulnerabilities, fortifying their defenses against malicious actors and safeguarding their digital assets.
- Penetration Testing: Building upon the findings of the vulnerability assessment, the penetration testing phase involves simulating real-world attack scenarios to determine the extent to which the identified vulnerabilities can be exploited. This phase provides valuable insights into the organization's overall security posture and the effectiveness of its defense mechanisms.
By integrating VAPT into their cybersecurity program, organizations can enjoy a multitude of benefits, including:
- Enhanced threat awareness: By understanding the tactics and techniques used by malicious actors, organizations can better prepare for and defend against potential attacks.
- Improved security posture: The insights gained from VAPT assessments enable organizations to prioritize and address their most pressing security vulnerabilities.
- Compliance and regulatory adherence: VAPT assessments often help organizations meet regulatory requirements and industry standards, reducing the risk of fines and legal penalties.
- Increased resilience: By continuously testing and strengthening their security measures, organizations can better withstand and recover from cyber incidents, minimizing the impact on their operations and reputation.
As the threat landscape continues to evolve, the demand for VAPT expertise will only continue to grow. By partnering with experienced security professionals, organizations can proactively identify and mitigate security risks, positioning themselves as leaders in the fight against cybercrime and safeguarding their digital assets for the long term.
Adversarial Simulation
Evaluating the resilience of systems and applications by subjecting them to realistic, adversarial attacks and scenarios.

Threat Emulation
Replicating the tactics, techniques, and procedures of known cybersecurity threats to assess an organization's ability to detect, respond, and mitigate such attacks.
Exploitative Verification
Testing the security of software and systems by actively attempting to identify and exploit vulnerabilities, weaknesses, or misconfigurations.

Automated Scanning
Continuously monitoring and analyzing systems, networks, and applications to automatically detect and report potential security issues or risks.
Attack Surface Mapping
Comprehensively identifying and cataloging all the potential entry points, interfaces, and exposure vectors that could be targeted by attackers.
Vulnerability Prioritization
Assessing and ranking security vulnerabilities based on factors such as severity, exploitability, and potential impact to focus remediation efforts on the most critical issues.
Services
/- Cyber Security
SOC as Service
Digital Forensics
VAPT
Offensive Security
/- Artificial Intelligence
Computer Vision
Chatbot and Conversional AI
Predictive Modeling
Data Analytics
Generative AI
Business Intelligence
/- Development
Web Development
Mobile Application
Cloud Solutions
DevOps and CI/CD
Game Development