Digital Forensics & Incident Response
In the ever-evolving landscape of cybersecurity, Digital Forensics has emerged as a critical discipline, enabling organizations to investigate and respond to security incidents with precision and rigor. This specialized field combines technical expertise, investigative skills, and a deep understanding of digital evidence to uncover the root causes of cyber attacks, gather admissible evidence, and support legal and regulatory proceedings.

Digital Forensics encompasses a wide range of techniques and methodologies, including the collection, preservation, and analysis of digital data from various sources, such as computers, mobile devices, and network logs. By leveraging specialized software and hardware tools, Digital Forensics professionals can recover and analyze even the most well-hidden digital traces, uncovering valuable insights that can aid in the investigation and resolution of security breaches.
One of the key advantages of Digital Forensics is its ability to provide a comprehensive understanding of the sequence of events leading up to and during a security incident. This information is crucial for organizations seeking to not only respond effectively to the immediate threat but also strengthen their overall cybersecurity posture and prevent similar incidents from occurring in the future.
Moreover, Digital Forensics plays a crucial role in supporting legal and regulatory compliance efforts. By following established best practices and maintaining the chain of custody, Digital Forensics experts can ensure that the evidence gathered is admissible in court, enabling organizations to pursue legal action against cyber criminals and comply with industry regulations.
As the frequency and sophistication of cyber attacks continue to escalate, the demand for skilled Digital Forensics professionals will only continue to grow. By integrating Digital Forensics into their overall cybersecurity strategy, organizations can enhance their incident response capabilities, improve their ability to identify and mitigate security vulnerabilities, and demonstrate their commitment to protecting their digital assets and safeguarding the privacy of their stakeholders.
Swift Incident Response
Our focus on rapid and effective cybersecurity incident response strategies minimizes the impact on our systems and data.

Legal Documentation
Precise and detailed legal documentation establishes a clear record of events, facilitating sound legal decisions.
Forensics Analysis
In-depth forensic analysis acts as a microscope, revealing the root cause and scope of the incident for optimal resolution.

Data Recovery
Our advanced data recovery capabilities can rescue valuable data even in critical situations, minimizing disruption and maximizing information retrieval.
Upgrade your Cyber Resilience
To stay ahead of the curve, continuous improvement of our cyber resilience and preparedness is key to effectively handling future security incidents.

Strategic Threat Mitigation
Our commitment to mitigating threats and fortifying our cybersecurity posture creates a powerful shield against future attacks.
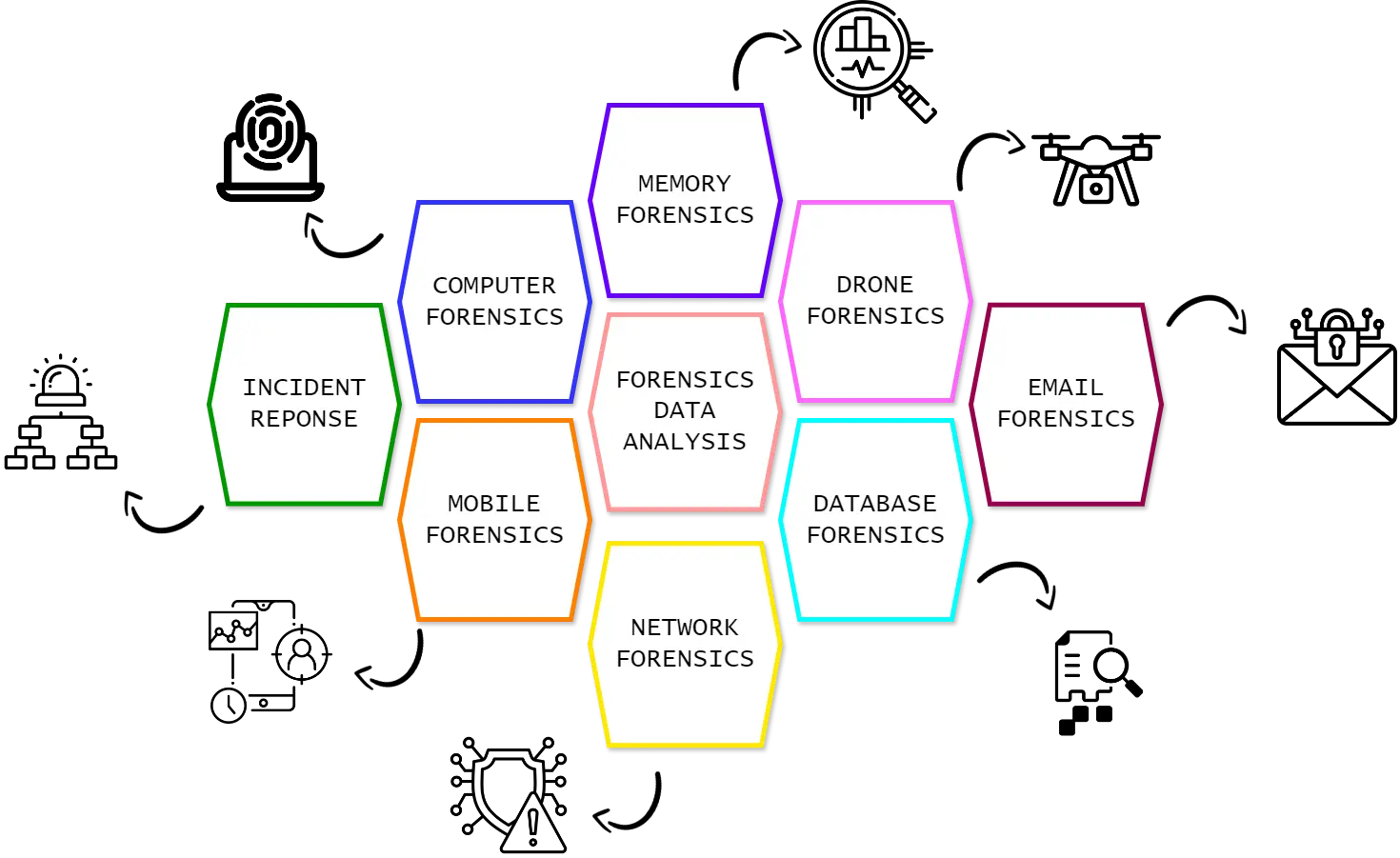
Services
/- Cyber Security
SOC as Service
Digital Forensics
VAPT
Offensive Security
/- Artificial Intelligence
Computer Vision
Chatbot and Conversional AI
Predictive Modeling
Data Analytics
Generative AI
Business Intelligence
/- Development
Web Development
Mobile Application
Cloud Solutions
DevOps and CI/CD
Game Development